Table Of Contents
How to stop Ransomware – As Ransomware is on the rise
New research has found that ransomware attacks have doubled in 2019 compared to 2018. So ransomware attacks are on the rise again.
If that’s not startling enough, hackers are using your own passwords to infect your systems with Ransomware. Continue reading to find out the possible methods on how to stop Ransomware.
What is Ransomware?
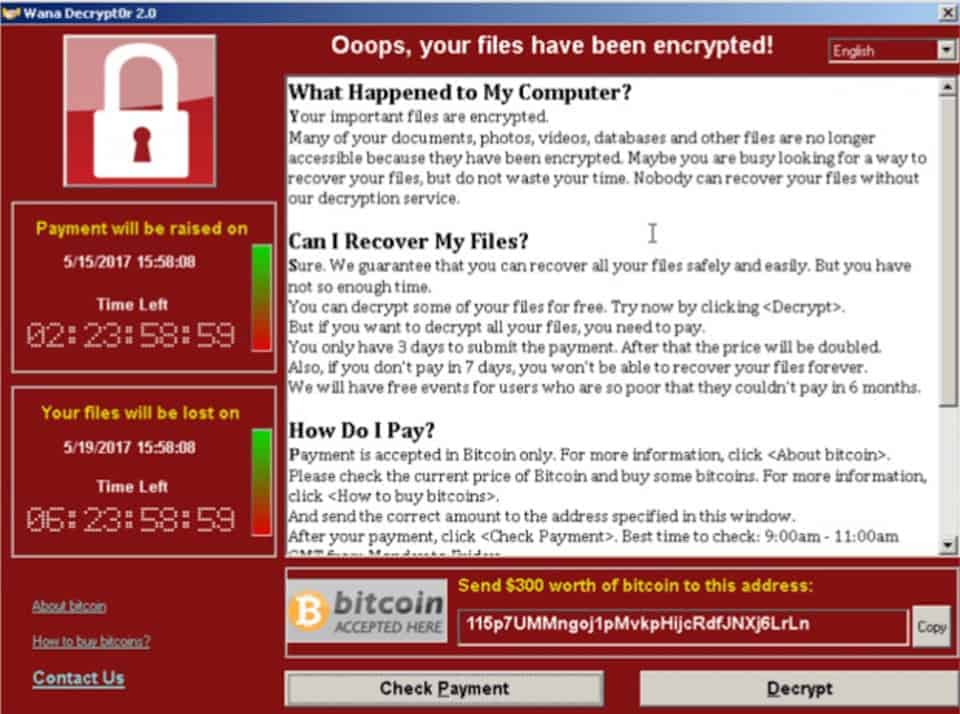
Ransomware is a type of malware that hackers use in Cyber-Attacks against your business. Ransomware encrypts your files and then the Cyber Criminals demand a ransom payment in return for a decryption key.
They will promise to decrypt your encrypted data after the ransom is paid but rarely do.
There are many different types of ransomware infection, with ransomware-as-a-service becoming more popular – this is a pre-packaged, easy-to-launch virus sold on the dark web for novice Cyber Criminals.
Other forms of ransomware include the infamous WannaCry attack which hit the NHS and other global businesses and Locky, which has been around for a long time.
Ransomware – Common Attack Methods
In a recent report, security researchers analysed ransomware attacks on honeypots
– servers designed to be appealing to hackers – during the first six months of 2019.
The research found that brute force attacks, whereby hackers attempt multiple logins using common or leaked passwords to break into accounts.
This overtook phishing and spam emails as the number one vector for infecting a business with encrypting ransomware.
31% of all ransomware attacks were the result of brute force attacks against Remote Desktop Protocols (RDPs).
Which, if unsecured, allow hackers to gain access to your business network and infect your servers and PCs with ransomware.
The increase in brute force attacks should be a wake-up call to businesses using weak or common passwords to secure their critical business systems.
Organisations should address their risk management policies to ensure sensitive information is protected against ransomware viruses.
What is the best defence against Ransomware?
Hackers will try to use the most common passwords, as well as those leaked in data breaches, to essentially hammer your systems with credentials until one works.
But if you think you’re safe because your credentials have never been leaked, or your password is complex and uncommon, the hackers can still get around that.
We wrote a detailed Guide titled The 9 Cyber Threats You Should Know About,
to make sure our customers are aware of the different ways it is possible for your passwords or security to be at risk.
You will find out that employees are often the weakest link when it comes to passwords, and the impact is so bad it will be predicted passwords as we know them will be dead in the coming years.
You might look at that last statement and feel a little hopeless; surely, in that case, they can crack any password? But you’d be wrong.
The key to your passwords is not complexity or how uncommon it is, but length.
That’s why we recommend passwords that are long but not necessarily jammed with complex characters; think of phrases you’ll definitely remember.
Depending on your password length, it may take billions of years to crack and you can find out more about that in our guides. It’s also critical to never re-use passwords.
If, for example, you used your highly secure password for your Yahoo account, which was breached, and re-used it for another service, hackers could easily crack that service too.
By adopting a password policy of using memorable phrases with no or limited complex characters, you’re far more likely to remember individual passwords and, thus, not feel the need to re-use them.
How do I protect my computer and how to stop Ransomware?
This isn’t to say you should focus solely on creating strong passwords to ensure good cybersecurity.
While phishing emails are no longer the primary vector for infecting victims with ransomware, they still account for a quarter (23%) of all successful attacks.
The other 46% include compromised firmware attacks, the download of fake installers, and hacking software.
These attacks can steal credit card data which can result in identity theft. The key to good information security is to make sure you have the right security installed.
While you must ensure you have secure passwords on your critical systems, it also evidences how many different methods hackers will use to infect your business systems and extort money out of you.
We strongly recommend you don’t pay the ransom if the hackers demand payment, as it’s very unlikely you’ll get your data back.
We strongly recommend you review your own password policies to avoid falling victim to a brute-force attack.
That could see hackers gain access to your internal systems and feasibly infect your entire network with malicious software.
But don’t forget to train your staff on spotting phishing emails or preventing the download of innocent-looking applications that could stealthily install malware, too.
Don’t know where to start? Why not talk to Hamilton Systems and our highly qualified security experts to understand how best to protect your business?
Get In Touch
Need expert IT assistance? Contact Hamilton Group today! Our specialists offer top-notch solutions tailored to your needs. Don’t let tech troubles hold you back.
Talk to us about your business 0330 043 0069
Or E-mail hello@hgmssp.com and one of our experts will get back to you.
Schedule A Quick Callback
The fastest way to figure out if we’re a good fit for your business is to have a quick chat about it. Schedule a 15-minute call so we can get right to the point.
Proactive, Responsive, Hamilton Group
Grab a drink and let’s have a quick chat about your business, and see how we can help you.
Book your call below or call us on 0330 043 0069


Carl Hamilton
A Message from our Founder/CEO
“We treat every client as if they were a part of our business to provide quality and comprehensive IT support that can be counted on 24/7, 365 days a year. We succeed only when you succeed.”
Let’s work together
IT Support You Can Trust
The best IT Support in Harrogate is also delivered across the UK 24/7 and we are ready to help you with all your Managed IT service needs. Services are provided in areas including Leeds, Liverpool, Manchester, Wakefield, Wetherby, York, Newcastle, Bradford, Bolton, Glasgow, Wigan, Derby, London, Luton, Birmingham, Sheffield, Peterborough, Portsmouth, Reading, Nottingham, Milton Keynes, Telford, and more.
Talk to us about partnering with an IT Support Company that cares
Move your business forward not back with HG.
Same Day Call-back.
Monday – Friday 09:00 – 17:30.
“Our email wasn’t performing very well so we asked Hamilton Group to take a look & Carl proposed to migrate us to MS Exchange.
Carl was very helpful throughout & the migration went very well.
He was on hand to sort out any teething issues, taking calls early morning & into the night, to ensure we were up & running smoothly.
Would recommend for knowledge, attention to detail & great customer service.”
Ian Porter
Fotofabric Limited